Many people are looking for building their own online blog.
One of the very popular online blog engines or websites, that had gained a lot of traction in the past, I would say 10 to 15 years, is WordPress.
People like WordPress because there is a huge community of developers, content creators around WordPress and because it’s open source. There are also a lot of plugins, a lot of themes and a lot of integrations with other services (payment gateway, cart, SEO …etc.)
You can even have an online store (e-commerce website) built on top of WordPress with free plugins. I think WordPress is pretty cool.
We at FaceGraph, have used WordPress to build our online store [https://shop.facegraph.com] that sold thousands of dollars of our products online and pretty much costs us 2 hours to setup!
The problem now is not the cost of WordPress itself since its open source, it is the cost of hosting WordPress. One of the things I liked in the past is the ability to host a WordPress website in the cloud for free. And to be clear, I am talking about the Microsoft Azure cloud.
WordPress consists today of two main components, the web server and a database which runs on MySQL.
In the past, if you have used Microsoft Azure. You were able to create an A WordPress blog using the Microsoft ‘WordPress’ listing in the Azure marketplace. That allowed you to create an app service plan to host the web component and more importantly also host the MySQL database in the same app service.
Unfortunately, that option is no longer available. If you go check the Azure Portal marketplace today, you will find there is only one title by WordPress “WordPress”. And there are many other word press titles by other companies.
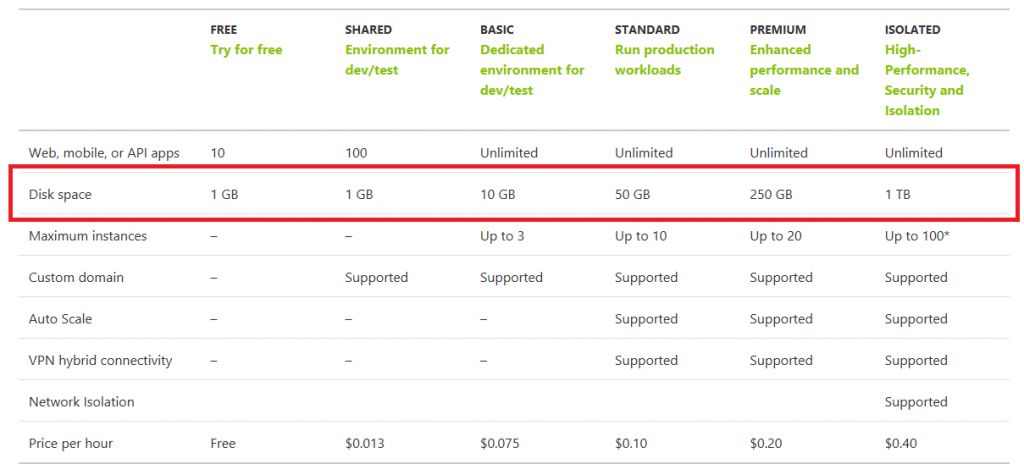
The WordPress listing allows you to create a WordPress blog for free, which is very convenient. However, it will basically create a new app service plan and it will also create a standalone Azure MySQL instance.
This setup might be good for production, heavy load, performant website. The cost of the hosting this setup will be about $146 a month.
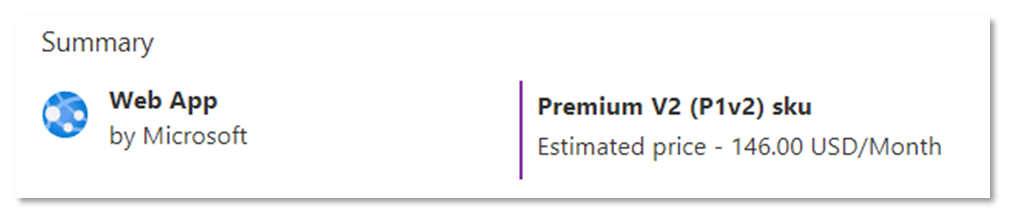
That might be hefty for someone who’s looking for an economical option.
If you want to have an economic option, an option to host a lightly accessed blog {like this one for instance 😊}, you may not want to consider a different option.
The solution
The solution to that is to use this ARM template WordPress on App Service with MySQL In App (microsoft.com) by Gerardo Saca.
This arm template will allow you to deploy the old WordPress title where you can have an Azure app service created uses the free tier by default and also have the MySQL database instance created in app.
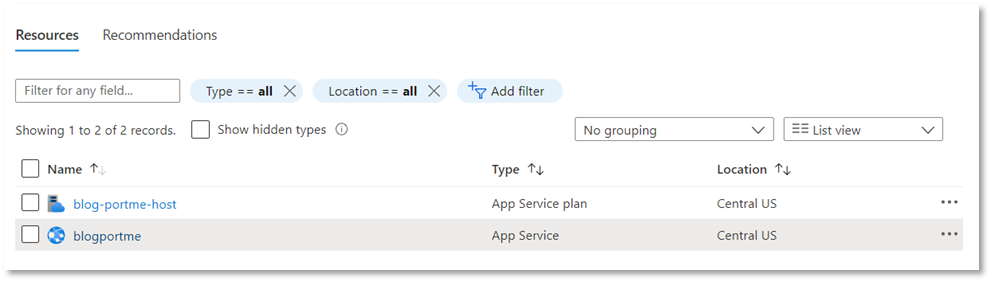
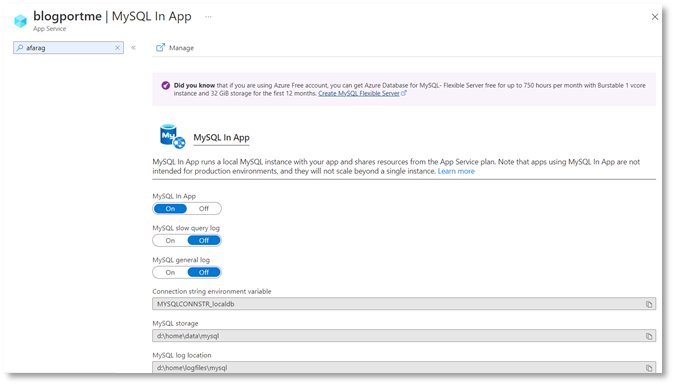
At the end of the day, you basically can pay nothing for hosting your WordPress website as you used to be in the past.
Obviously, needless to say this is not really an ideal setup for production. You bear the risk of losing your database without redundancy, the performance will also be impacted since you share the App service plan resource between the website and the database. However, it’s a good cheap option, it works and takes 5 minutes to setup!
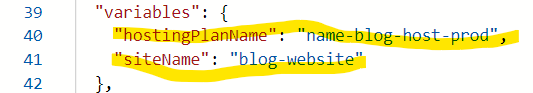
To be a good citizen of Azure, and follow your whatever governance and naming convention you may have, I would strongly recommend you to edit the template before your deploy it, locate the following two variables and updated them with your own desired name for the app service plan as well as the web app service name:
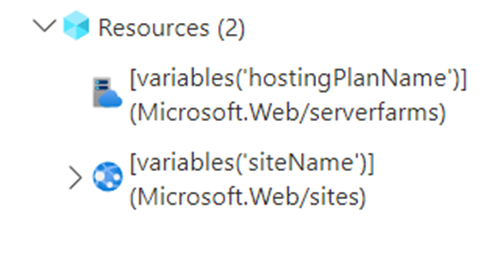
For instance you can change them from this:
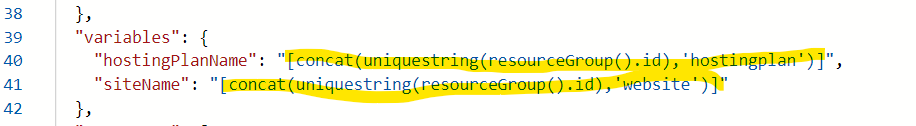
To this:
Lastly, one of the things you will want to do in your WordPress blog is to change the look the appearance. You probably will look for existing themes or maybe try to import a new theme.
Check this website. https://elements.envato.com which has a huge library of electronic marketing assets and great themes for WordPress.
One of the things you’re going to face when you try to import a theme that has a lot of graphics especially if it’s big say around 10-15 MB is a problem importing the theme zip package.
You will get an error message like this:
“the page was not displayed because the request entity is too large.”
To fix this issue you have to change the settings of your web server to allow larger requests. If you have hosted your application on a Windows based app service. This is how you fix it. You add this configuration in the web.config:
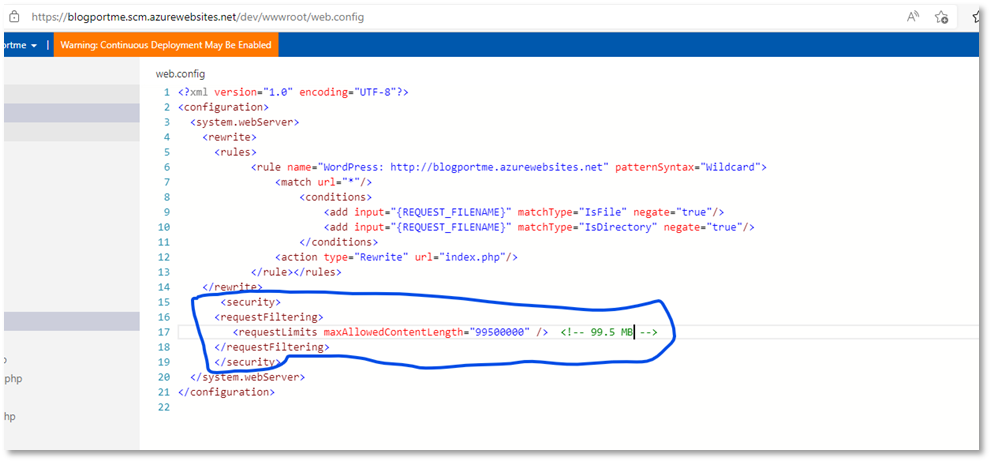
<security>
<requestFiltering>
<requestLimits maxAllowedContentLength="99500000" /> <!-- 99.5 MB -->
</requestFiltering>
</security> I hope that in-app hosting of MySQL continues to be available as it saves a lot of money (in this case 100% of cost) for hosting a WordPress blog.
The question now is, can you do this in AWS?